SketchUp Pro Crack is a powerful 3-D building application application for a severe variety of sketching applications. Be conscious of the most recent update of this application to provide awesome brand-new points. You can make three-D sketching much less difficult. They have a clear appearance characteristic that ought to now make quicker as well as present top quality. It allows you just about all the software you would like to produce all kinds of two-D as well as 3-D creating.
You may visit the website for more free cracks: key4pc
SketchUp Prthe o Crack is utilized for woodworking plans, the town as well and MetropolitaDownloadsg styles. SketchUp Pro 2022 Free Download is significantly better at showing several transparencies to offer a lot more perceptions of a level throughout a number of the see-via encounters. SketchUp Pro Crack is greatest for two-D as well as three-D movie video game styles. We have added the e capability to hone the opacity degree in the X-ray set. We have added the e capability to hone the opacity degree in the X-ray set.
Sketchup Pro 2022 Crack + License Key Download [Latest]
SketchUp Pro License Ka ey 2022 is a beginning 3D style as well as a modelling system. SketchUp Pro Crack is a rival with h Windows TEN, Seven, Eight, & Vista, with WithSIXTY-FOUR Complete versions (THIRTY-TWO to SIXTY-FOUR bits). These types of coming with various web template kinds, 3D SketchUp Pro Crack Stockroom. SketchUp Prto o Crack is simple to use as well as simple to install. SketchUp Pro CrackPro’s Latest Version has toked a full residence map for you personally on the foundation of your specifications such as home, design and style, thickness, higher, areas and so on.
SketchUp Pro Serial Key allows you to generate 3D versions of home woodworking tasks. SketchUp Pro Crack is the greatest option for a CAD software program that is very complex. SketchUp Pro Crack is great for 3D publishing, civil well as home creating every 3D version. This system is very difficult for inexperienced people In this most recent edition developer of this fantastic software 3D Studio Max provides a lot of features for very simple modeling. The most appealing feature is the ability to plug into Google Earth.
SketchUp Crack License Key 3D Modeling Software 2022
Sketchup Pro 2022 has just about all the capabilities that you need such as the regular sketching equipment and filling up results. They have full fine detail about design and style, standards as well as plans simply such as a thousandth of A. SketchUp Pro Crack does not necessarily mean it does not have options. The design is simply because these view-ports are inhaling and exhaling the sights of the task. Are accessible on the food selection. Designing home interiors and exteriors are presented in this program.
A user can access online designs in 3D from an online database containing various design works. All models in the software can be customized. SketchUp Pro provides full support to its users to practice all construction, graphics, drawings, and construction designs easily. CAD is a great piece of engineering application software that allows architects and civil engineers to create, edit, and share 3D models. Designers on the web use this software product a lot. Delivering out the description into an additional device such as AutoCAD can beat the problem.
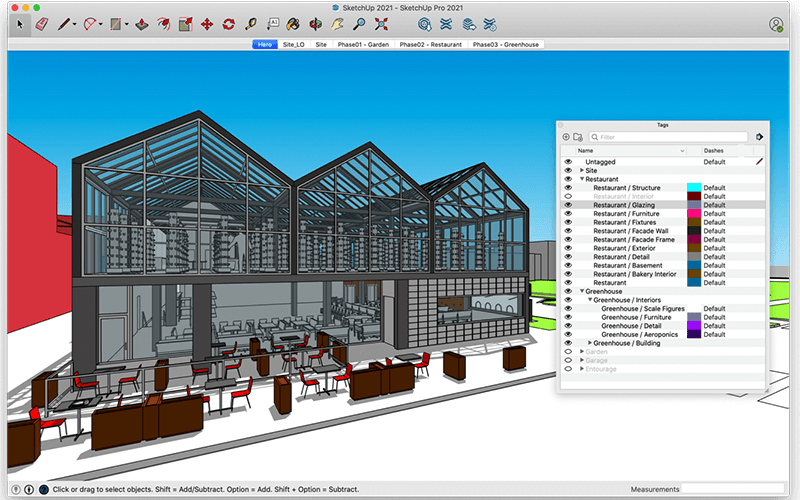
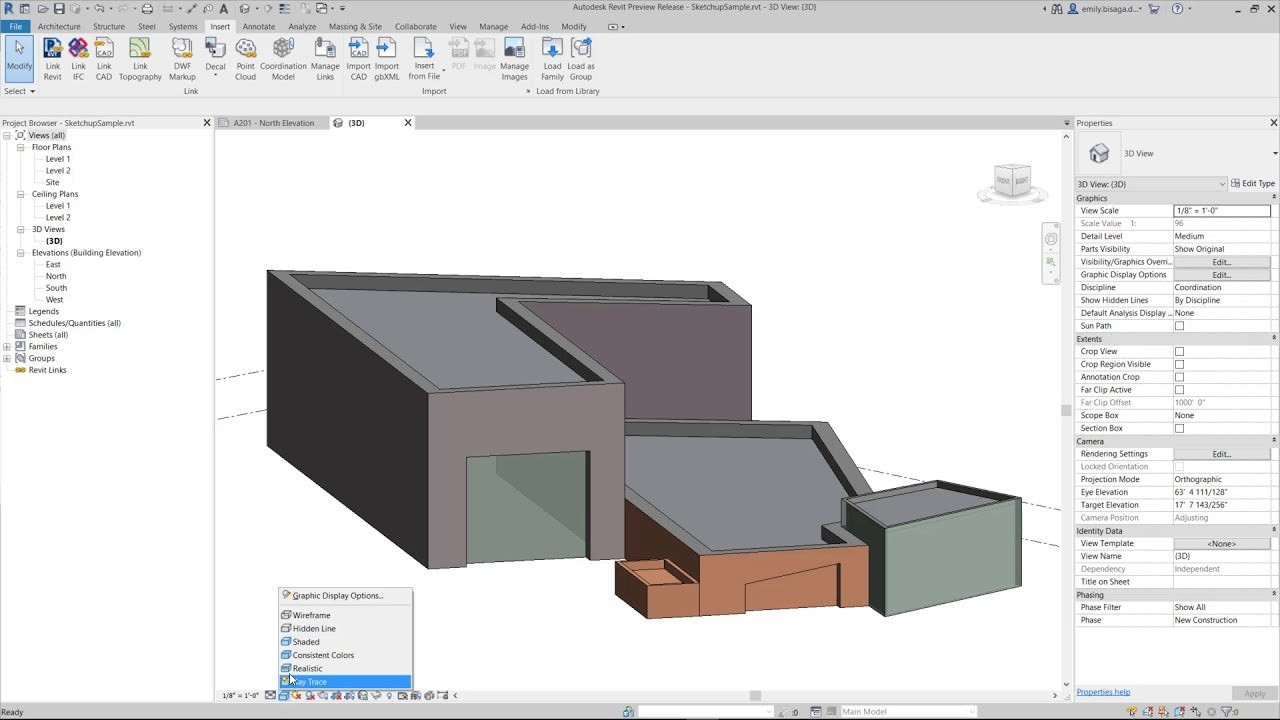
Sample Image:
Features Key Of SketchUp Pro 2022 Crack:
- Sketchup Pro 2022 Free Download works 100% when it comes to creating the best 2D and 3D photos.
- It comes with over 2There new compositing resources.
- There are more than 50 assorted style designs that are available to customers.
- Product performance is generously best in class and latest.
- In addition, the device comes with a built-in 3D audience to make the product affordable for customers as a theme and photo description studio.
- Making use of the Layouts chat, you can select multiple as well as fills and turn them
- into layouts.
- The user interface of the device is much more important, as the complexity of its advanced features is well known.
- Microsoft’s 3D modelling software is available for Windows and Mac computers. With it, you can design and draw more easily.
- Civil engineers and mechanical engineers will also find this app useful.
- Imagination is transformed into 3D models using its powerful features.
- A variety of 3D projects can be created with this intuitive program. Create programs quickly and easily.
- Understand the new 3D mod, eling design of the user.
- With this program, you can create an automatic 3D CAD document.
- Therefore, planning in three dimensions is also possible.
- The use of this material is beneficial for internal construction. Make sketches of your ideas.
What’s New In SketchUp Pro Crack?
- it provides many fresh offset functions for self-intersecting geometry in addition to preventing all overlapping. Using this, you thoroughly clean all balance.
- A customer can take advantage of this application to distort your product into a powerful walk via.
- 3D Modelling applications, innovative styles tools with clear symbols Replicate film camera positions and discover your designs directly.
- Hundreds of ins are precise, so it is possible to style, identify, and plan with small details. Obtainable in numerous diverse languages such as English, Chinese, German, French, Korean, Italian, Colonial, Spanish, etc.
- using this, it is possible to add inference.
- With this particular, you can take perpendicular photos with image canal facilitates.
- It truly is for both experts and along with unskilled.
- Style the easiest yet clearest product with razor-sharp sides.
System Requirements:
- Intel 64-bit 2GHz processor.
- 2GB or better.
- More than 500 MB of the free hard disk.
- Unlock 1.5 video cards with at least 128 MB of the latest models.
- Web navigator.
- Internet link.
How To Crack?
- Download the setup and crack provided below
- Extract it and run the installation
- Perform the installation and wait for it to complete.
- Then click the Activate button
- Now copy the crack files and paste them into the installation folder.
- That’s all Ready.
- Enjoy premium features.
Link: SketchUp Pro